So here’s something most people in the know will tell you about setting a strong password: length beats complexity. A 30 character password made up entirely of lowercase letters is going to be more difficult for an attacker to break (whether by brute force guessing passwords on an online login page or cracking password hashes compromised in a data breach) than an 8 character password with the requisite mix of upper case and lowercase letters, numbers and special characters.
What’s really convenient and almost mind-blowing about this is the former kind of password is actually much, much easier for people to memorise. This well known xkcd comic explains it best.
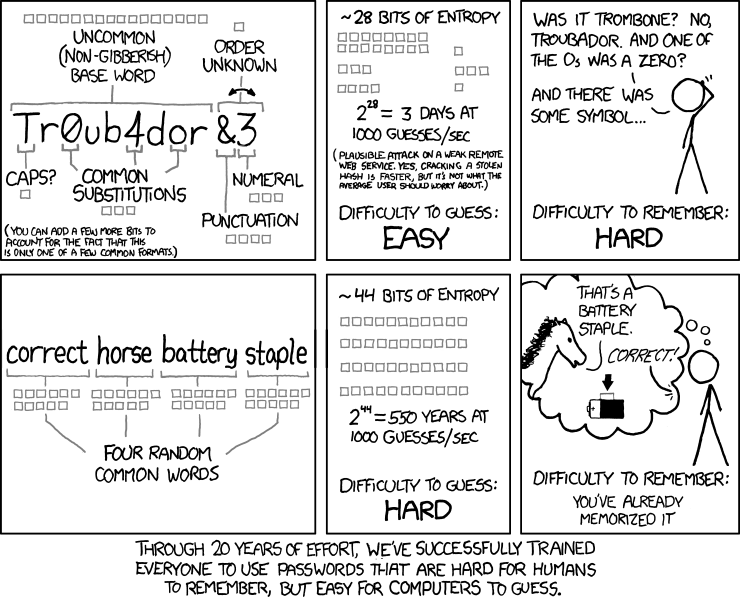
And yet the model of a secure password policy goes something like this:
- Eight characters minimum.1
- At least one: uppercase letter, lowercase letter, number, and special character (!@# $%^!@…).2
And sometimes also:
- No sequences. (eee, 111, 123, abc, etc…)
- No dictionary words.
- Contains no part of your username or the website name.
Ryan Winchester writes that these sorts of strict rules are more a hindrance than good security, and I’m inclined to agree. The idea, as Winchester says, is to get users to set random passwords like, let’s say, jNhb%cdx9a, but it’s fundamentally misguided because human beings are a poor source of entropy. That random password example I gave? That’s basically just a zigzagging keyboard walk with a couple of tricks, hardly more random than qwerty. This internal logic and lack of randomness makes it much easier to remember than something like 7%OBgblv7ahz9ay9: memorability being an essential component of most password choices (yes, I’ll get to password managers just now).
Your password policy defines the password most of your users are going to set. Password123! will pass most apparently strong, secure policies, and if it will pass, it will be set. Humans will, in the majority of cases, put the required uppercase character at the beginning of the password, and the required numbers and specials at the end. The particularly industrious may go one further and perform obvious substitutions like P@$$w0rd, but you’re not going to get anything approaching true randomness, because passwords have to be invented and then remembered.
Even if you can come up with something approaching real randomness3, it’s dead in water if it’s less than eight characters long, because computers are getting pretty good at quickly brute-forcing random strings these days.
So the solution that we’ve come up with is passphrases: make your password a long string of dictionary words that (1) you can remember (because humans are good at remembering words and phrases) and (2) is long enough that the entropy sorts itself out despite your human randomness failings.
In light of all this, Winchester ultimately recommends dispensing with the complicated characterset rules and just making the password requirement a certain level of entropy and dissimilarity to common words and passwords ala How Secure is My Password?4 or Dropbox’s zxcvbn. But how well do these things work in practice?
Something like maryhadalittlelamb, despite getting an all-green “233 million years” from How Secure, would certainly be cracked very quickly by anyone savvy enough to try cracking with a dictionary of common phrases. The xkcd/Snowden–propagated passphrases meme comes with the unspoken and often omitted asterisk that your passphrase has to be unique. Common phrases aren’t going to save you.5
So where does this leave us? Passwords are an arms race. As more and more people start using passphrases, more of the cracking focus will go into cracking passphrases. Scrape the web for song lyrics; .downcase and .join a few different combinations; see what comes out. I think this is going to become more common as the idea of passphrases slowly filters down.
Also: strong passphrases are just one element of password security. It’s also important to never reuse your passphrases. New account, new passphrase. And that means no variations on a root phrase!
And don’t put all your trust in your passphrase either. If it’s an important account, like your email or something that has your card details, use two-factor authentication.
Finally, to reduce the burden on your human imagination and memory, I think it’s a really good idea to use some sort of password manager like KeePass/pass or LastPass/1Password (depending on your feelings about the cloud) and generate random 16+ character passwords for most of your accounts. With that, you can save your passphrases for things like your OS user account, drive encryption and, of course, the password manager itself. You can also opt to focus your limited powers of human randomness on passphrases for a few critical services, if you don’t like the single point of failure password managers introduce.
The other benefit of password managers is that they make it really easy to change your passwords. When my phone got stolen earlier in the year, changing all my passwords6 was just a matter of going through the list and clicking a few things to generate new passwords: no need to invent tens of wholly new, wholly original passphrases.
So, summary: passphrases are better than passwords, but you still have to be inventive, and they probably don’t scale. Humans are bad at randomness. Autogenerate as many passwords as you can.
-
If there’s a maximum limit not measured in hundreds of kilobytes, the site probably isn’t hashing your password like it’s supposed to, and instead storing it in plaintext in a varchar(20) field. ↩︎
-
Unless the site has bad input validation, in which case special characters are explicitly disallowed. And if they’re bad at regex, you could end up being forced to have exactly one of each characterset. ↩︎
-
Turing Award or not, this is very bad advice. ↩︎
-
Also, that site tells you how long it would take a (presumably average) desktop PC to crack a given password, not how long it would take a dedicated GPU cluster. ↩︎
-
But let’s not forget that even a common passphrase is better than a common password. ↩︎
-
I remote-wiped the phone first, but it pays to be careful about these things. ↩︎
 David Yates.
David Yates.