If you’re serious about the security of your data, it’s not a bad idea to encrypt your hard drive. For the cost of an extra password-entry on startup, you’ll be assured that no-one can get ahold of your data even if they steal your device.1 There are facilities for doing full disk encryption on both Windows and Linux.
For a couple of years now, the Ubuntu install wizard has provided the option of encrypting your install with the check of a box. Easy and hassle-free.
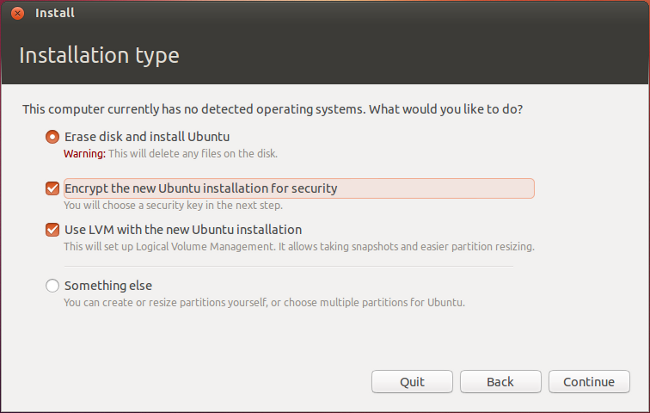
Well, almost hassle-free.
With the rise of solid-state drives, most modern computers contain at least two hard drives – an SSD for installing the OS to so you get that sweet nigh-instant boot time, and an HDD for doing most of your file storage, because large (>256GB) SSDs are still impractically expensive for most people.
So you can probably see where the trouble comes in. Sure, the Ubuntu installer allows you to encrypt your installation, but if that’s on your SSD it leaves your HDD (with the majority of your storage space) unencrypted. Not quite ideal.2
Thankfully, there’s a way to encrypt your extra drive after installation, and a few tricks to make it as seamless as if you’d done so in the first place.3 Here’s how:
If you haven’t already, install gparted (a popular Linux program for graphically formatting disks and editing partitions). Open GParted and delete all partitions on the disk you want to encrypt (make sure it’s empty beforehand!). Then create an unformatted partition in place of everything you just destroyed.
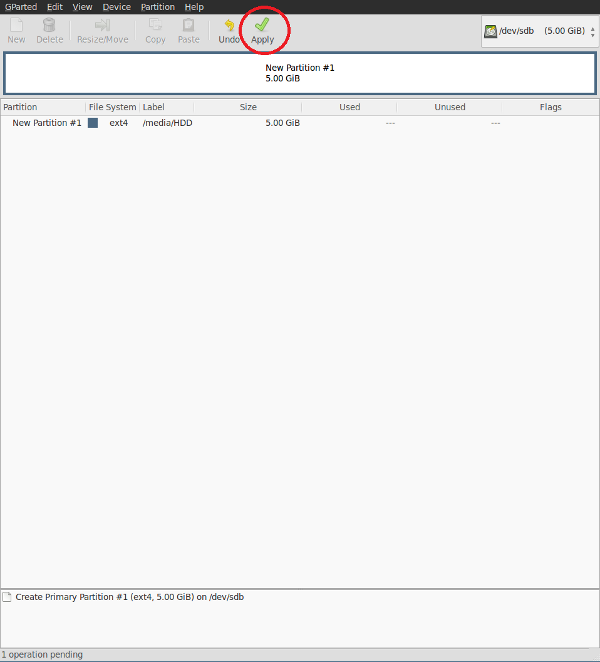
Screenshot taken from virtual machine. If you’ve actually got a 5GB HDD, I’m sorry.
Due to the potentially dangerous nature of GParted’s operations, you’ll need to click “Apply” after you’ve instructed the program to do what you want in order to physically perform the partition destruction and creation. No one-click format here (thankfully).
Once that’s done, it’s time to encrypt the partition. Open a terminal and run LUKS cryptsetup to do this (replace sd?X with the name of the partition to encrypt – for example, sdb1 or sdc2). All the necessary programs should already be installed if you’re running standard Ubuntu.
sudo cryptsetup -y -v luksFormat /dev/sd?X
Then you’ll need to decrypt the new partition so that you can format it with ext4, the modern Linux filesystem preferred by Ubuntu.
sudo cryptsetup luksOpen /dev/sd?X sd?X_crypt
sudo mkfs.ext4 /dev/mapper/sd?X_crypt
Now you can mount your new encrypted partition. The mount point can be anywhere you want, but you’ll probably want to put it either in /media/<some-folder> or /home/<your-name>/<some-folder>. You’ll need to create some-folder before mounting (make sure it’s empty!).
sudo mount /dev/mapper/sd?X_crypt /<mount-point>
Technically speaking, this is all you need to do encrypt your second harddrive. It just means that you’ll have to manually mount and decrypt it every time you want to use it. If you’re using it to store sensitive, rarely used data, that might be perfect.
But if you actually want to use it as a regular, frequently accessed harddrive, there’s a way to automatically mount and decrypt your second drive on startup, when your primary harddrive is decrypted.
First you’ll need to create a keyfile, which acts as a password that you don’t have to type in every time you start up (like your primary harddrive encryption password).
sudo dd if=/dev/urandom of=/root/.keyfile bs=1024 count=4
sudo chmod 0400 /root/.keyfile
sudo cryptsetup luksAddKey /dev/sd?X /root/.keyfile
Now that the keyfile’s been made, you’ll need to add the following line to /etc/crypttab to automatically use it to unlock the partition on startup.
sd?X_crypt UUID=<device UUID> /root/.keyfile luks,discard # (New encrypted partition with keyfile that was generated)
To get your parition’s UUID, use this command (you need to sudo it so that all of your partitions show up):
sudo blkid
The value you want is the UUID of /dev/sd?X, not dev/mapper/sd?X_crypt. Also make sure to copy the UUID, not the PARTUUID.
Then you’ll need to add this line to /etc/fstab to actually mount the partition on startup.
/dev/mapper/sd?X_crypt /<mount-point> ext4 defaults 0 2
Then restart and everything should work. If you find yourself unable to create files in the new partition, it’s probably still owned by root and needs to be chowned to your user. Run this command:
sudo chown <user>:<user> /<mount-point> -R
And there you have it, full disks encryption that just works.
Just so long as you use a strong password. As you’ll have to type it in every time you start up your PC, I recommend something lengthy but memorable. ↩︎
If anyone knows a way of easily encrypting more than one drive from the Ubuntu installer, please tweet me about it. ↩︎
Thanks to some colleagues for showing me this. ↩︎
 David Yates.
David Yates.